Project summary
IBM Cloud File Storage enables applications to easily store, organize, and share files securely. I worked on a crucial feature called “encryption-in-transit,” which protects file storage data from eavesdropping, interception, or tampering while data is being transferred between networks.
As design lead, I led multiple workshops and collaborated with engineering to map the proposed technical solution to the back end, which revealed major user pain points. These exercises successfully convinced the team to pivot to a more user-centered solution, which we then validated through 11 stakeholder and user interviews.
Results
61.5% decrease
in total number of user steps required compared to the initial technical implementation that was proposed
6+ months
of estimated technical & UX debt prevented
Identifying the problem
Problem space
A virtual server instance (VSI) is essentially a computer that you rent remotely from a cloud provider.
File storage is a type of storage best used for sharing data across multiple virtual server instances in the cloud.
Together, VSIs and file shares allow businesses to work collaboratively, share files efficiently, and scale operations easily, without having to own and manage their own physical servers and storage devices.
However, one challenge with this convenience is making sure that the connections between VSIs and file shares are secure over the public internet.
Challenge
How can we enable customers to easily encrypt their data in transit when using IBM Cloud File Storage so their data stays secure?
Mapping user flows to the back-end to create clarity
I was brought in when the engineering team already had a first draft for how they’d enable encryption-in-transit for file storage users.
To better understand the space from a user standpoint, I led a series of workshops with the engineering team to co-create a service blueprint map that put the user interactions and IBM back-end together into one view.

Discovering a borderline-unusable experience
After the mapping, I began asking clarifying questions and discovered a few pain points.
To enable encryption in transit between file shares and VSIs, users have to renew something called security certificates at least yearly. If those certificates expire, users start seeing application errors and downtime.
There were issues with certificate renewal in the originally proposed flow:
Lack of notifications and system visibility
Users could not be notified that their certificates that would expire soon, or that they needed to renew their security certificates.
Users could not be notified that their certificates that would expire soon, or that they needed to renew their security certificates.
Users wouldn’t know which certificates expired
Telling users which particular VSIs had expired certificates was also impossible due to a technical constraint.

In short, with the initial solution, the customer experience after initial setup was borderline unusable.
By getting the team to talk through the end user experience, and highlighting user pain points alongside the technical details, I successfully convinced the engineering team to explore alternative solutions.
Pivoting to a more user-friendly solution (automation)
Once the architects regrouped and had a new proposal, I worked with them again to map it out in another service blueprint.
The new experience used a utility tool called a file share “mount helper utility tool,” which allowed customers to download and install the software on their virtual servers from IBM’s open source library.
When users run the tool on their servers, the automated mount helper automatically completes the initial setup steps and handles all required maintenance afterwards 🎉

Summary of changes
ㅤ | First-time setup phase | Maintenance phase | Total steps |
Without mount helper (initial proposal) | 9 steps | 4 steps (many of these steps were near-impossible and would require a lot of guesswork) | 13 steps |
With automated mount helper | 5 steps | 0 steps, because it was entirely automated ✨ | 5 steps |
The number of steps reflect real data from the project, not what you see in the representative service blueprint maps above.
Concept validation
We presented this new solution to the VP of development for IBM Cloud Storage, who liked the proposal but raised concerns about whether IBM's most security-conscious customers would want to use an open-source mount helper tool.
I worked with our UX researcher to plan and conduct a research study evaluating the security of the new mount helper approach. In the span of 2 weeks, we conducted and synthesized a total of 11 interviews with IBM subject matter experts and external IT professionals who had experience with cloud file storage and maintaining security.
We actively involved our software architects during planning and invited them to the interviews so they could ask follow-up questions and help guide interviews with their expertise.
Key findings
Our most security-minded customers would be okay with an open source mount helper utility as long as it meets their compliance and security requirements and its behavior is well documented and transparent.
Even in the overall cloud industry, keeping track of when security certificates expire* is a common pain point for many users, particularly when it comes to monitoring and managing certificates at an enterprise scale.
*required for maintaining secure connections between a file share and virtual server
*required for maintaining secure connections between a file share and virtual server
Recommendations
Proceed with the open-source mount helper utility tool, making sure it is implemented securely and that the code is documented transparently.
Allow users to easily customize the mount helper tool to meet their own needs if they need more control and security. We provided guidance in documentation and hosted the tool on GitHub so developers could easily evaluate and modify the software.
Final solution
What would’ve been a very complex and near impossible user flow without the automated mount helper ended up being a relatively simple experience.
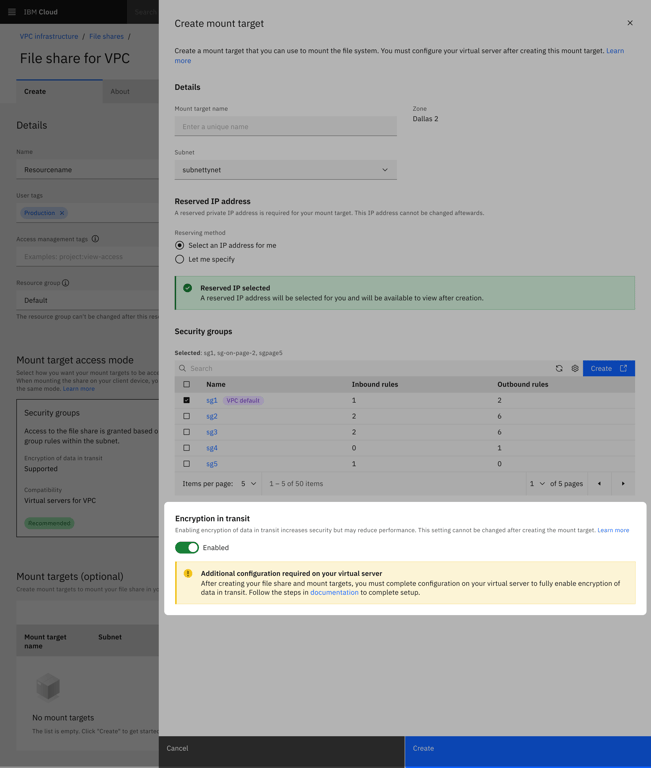
In the UI, I simply added a toggle option while creating a file share connection to a virtual server:
Users would still need to perform some standard steps outside of IBM’s interfaces by logging into their virtual server instance and running the mount helper software. I highlighted this guidance on the details page of a file share with a link to the relevant documentation:
Outcomes
This Encryption in Transit feature launched in August 2023 as part of the IBM Cloud VPC File Storage release 🎉
61.5% decrease
in total number of user steps required compared to the initial technical implementation that was proposed
6+ months
of estimated technical & UX debt prevented
Summary of flows
During a retrospective I conducted with the team, we also received excellent feedback from team members who were eager to participate in more design-thinking processes like this:
“Mural with UX flow diagrams were really helpful [in reference to the service blueprint maps co-created in our virtual whiteboarding tool].”
— Software engineer, IBM Cloud Storage
“Interviewing people outside of the Org to gather requirements and feedback is a very good idea.”
— Software engineer, IBM Cloud Storage
Product awards
This streamlined experience was also a factor in VPC File storage winning 2 awards after the service went Generally Available:
2024 Cloud Stratus Award by Business Intelligence Group

2024 Good Design Award winner
Multimedia category
Multimedia category

Reflection
This project made me recognize the impact of “making to think.” This service blueprint is now one of my go-to design activities for complex technical spaces because it:
- helped me understand the domain just enough for me to ask more informed questions about the user experience (outside of just IBM Cloud interfaces)
- built trust between design and engineering teams because I brought them into the process specifically asking for their expertise
- brought much-needed alignment and clarity more quickly than multiple verbal-only meetings
- helped us pivot to a new solution that drastically benefited the user experience and reduced technical debt down the road
