Summary
In today’s digital landscape, efficient and secure file storage is crucial for anyone using the cloud. IBM Cloud File Storage allows users to easily store, organize, and share files securely. My team worked on a crucial feature called “encryption-in-transit,” which protects file storage data from eavesdropping, interception, or tampering while data is being transferred between networks.
As design lead, I led multiple workshops and collaborated with engineering to create a service blueprint map. I identified and presented major user pain points in that mapping to the engineers, successfully convincing the team to pivot to a more user-centered solution which we then validated through 11 stakeholder and user interviews.
61.5% decrease
in total number of user steps required compared to the initial technical implementation that was proposed
6+ months
of estimated technical & UX debt prevented
Identifying the problem
The situation
I was brought in when the engineering team had a first draft for how they’d enable encryption-in-transit for file storage users. As they walked through it with me, I heard a number of confusing technical terms and concepts like “VPN certificates” and “certificate lifecycle management,” none of which made sense to me at the time.
Before I could even design anything, I needed to get myself up to speed on those concepts and understand how customers would interact with our back-end in the proposed solution.
Problem space & context
File storage is a type of storage best used for sharing data across multiple virtual server instances in the cloud.
A virtual server instance (VSI) is just a computer that you rent remotely from a cloud provider.
Together, VSIs and file shares allow businesses to work collaboratively, share files efficiently, and scale operations easily, without having to own and manage their own physical servers and storage devices.
One challenge with managing things virtually, however, is making sure that the connections between VSIs and file shares are secure over the public internet. As the product design lead, I worked with a team of engineers, product managers, and researchers to build functionality that lets customers protect their file storage data in transit.
Challenge
How can we enable customers to easily encrypt their data in transit when using IBM Cloud File Storage?
Creating the initial service blueprint
To better understand the space, I led a series of workshops with the engineering team to co-create a service blueprint map which put the user interactions and IBM back-end together into one view.
Once we had the basic tasks and flows mapped out, I walked through it again with the engineering team, this time asking questions for clarity about the user experience and highlighting pain points with appropriate emojis.
Pain points with the initial solution centered around the post-setup and maintenance phase, which lacked useful notifications due to technical constraints. (If you’re interested in more details, expand the optional sections.)
- Optional: Additional glossary of terms (1 min)
- Optional: Detailed pain points (1 min)
A service blueprint map of the first solution proposed by the engineering team. Click the image to view it larger, or to view detailed steps, check out the unannotated PDF ↗️.
Diving into these technical details alongside the user experience and pain points ultimately convinced the engineering team to consider an alternative solution.
Pivoting to a more user-friendly solution
Once the architects regrouped and had a new proposal, I worked with them again to map it out in another service blueprint. The new experience used a utility tool called a file share “mount helper utility tool.” This mount helper required customers to download and install the software on their virtual servers from IBM’s open source library.
When users run the tool on their servers, the mount helper would automatically complete the initial setup steps and handle all required maintenance afterwards.
- Detailed pain points eliminated
A service blueprint map of the final concept that we pivoted to. The majority of steps are now on the back-end since maintenance is entirely automated after a user runs the mount helper during first-time setup. View larger (PDF)↗️
Concept validation
We presented this new solution to the VP of development for IBM Cloud Storage, who understood the need for the pivot, but was concerned about whether IBM's security-conscious customers would want to use an open-source mount helper tool.
I worked with our UX researcher to plan and conduct a research study evaluating the security of the new mount helper approach. In the span of 2 weeks, we conducted and synthesized a total of 11 interviews with IBM subject matter experts and external IT professionals who had experience with cloud file storage and maintaining security.
We actively involved our software architects in the interview and planning stages so they could ask additional follow-up questions and help guide interviews with their expertise.
Key findings
Our most security-minded customers would be okay with an open source mount helper utility as long as it meets their compliance and security requirements and its behavior is well documented and transparent.
Keeping track of security certificate expirations* is a common pain point for many users, particularly when it comes to monitoring and managing certificates at an enterprise scale.
*required for maintaining secure connections between a file share and virtual server
*required for maintaining secure connections between a file share and virtual server
Customers in companies with larger teams tend to want more transparency, control, and customization than smaller customers who often prefer more out-of-the-box solutions. Larger customers also tend to have more technical staffing to build and design their own tooling to their liking.
Recommendations
Proceed with the open-source mount helper utility tool, making sure it is implemented securely and that the code is documented transparently.
Allow users to easily customize the mount helper tool to meet their own needs (e.g. for even greater security). We provided some guidance in documentation and hosted the tool on GitHub so developers could easily evaluate and modify the software
Final solution
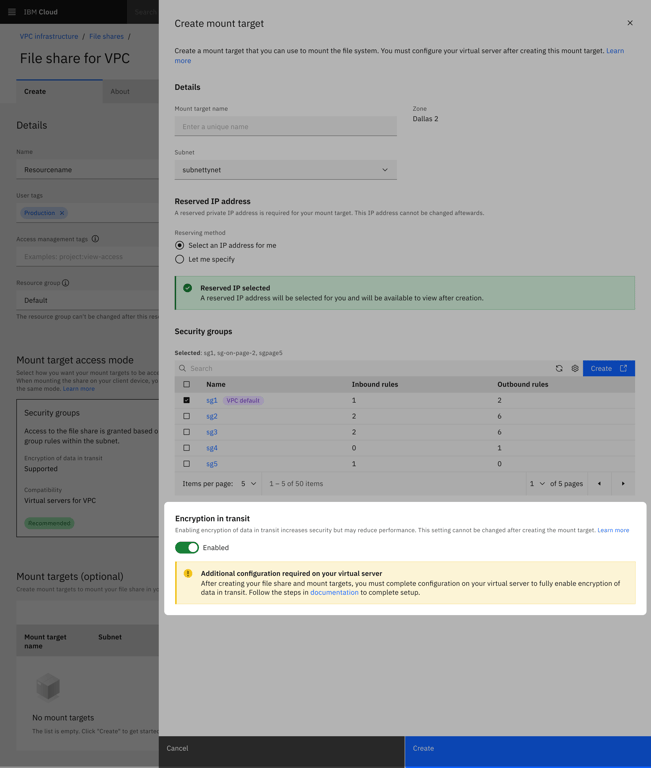
What would’ve been a very complex and near impossible user flow without the automated mount helper ended up being a simple toggle while creating a file share connection to a virtual server:
Users would still need to perform some standard steps outside of IBM interfaces by logging into their virtual server instance and running the mount helper software if they wanted to use it. So I highlighted this on the details page of a file share with a link to the relevant documentation.
Outcomes
This Encryption in Transit feature launched in August 2023 as part of the IBM Cloud VPC File Storage release 🎉
61.5% decrease
in total number of user steps required compared to the initial technical implementation that was proposed
6+ months
of estimated technical & UX debt prevented
Summary of UX impact
ㅤ | First-time setup phase | Maintenance phase, or when things go wrong | % Difference |
Without mount helper | 9 steps | 4 steps (many of these steps were near-impossible and would require a lot of guesswork) | 44.4% decrease in number of steps |
With mount helper | 5 steps | 0 steps, because it was entirely automated! | 100% decrease in number of steps |
During a retrospective I conducted with the team, we also received some great feedback from team members who were eager to participate in more design-thinking processes like this:
“Mural with UX flow diagrams were really helpful [in reference to the service blueprint maps in our virtual whiteboarding tool].”— Software engineer, IBM Cloud Storage
“Interviewing people outside of Org to gather requirements and feedback is a very good idea. We should make this standard for UI and feature design for major features.”— Software engineer, IBM Cloud Storage
Reflection
This project made me recognize the impact of “making to think.” This service blueprint / journey map is now one of my favorite design activities for complex technical spaces because it:
- helped me understand the domain just enough for me to ask more informed questions about the user experience (outside of just IBM Cloud interfaces)
- built trust between UX and engineering teams because I brought them into the process specifically asking for their expertise
- brought much-needed alignment and clarity more quickly than multiple verbal-only meetings
- helped us pivot to a new solution that drastically benefited the user experience and reduced technical debt down the road
If you’re interested in learning more, trying this for your own projects, or just have feedback / want to talk shop, don’t hesitate to reach out to me at alissa14chan@gmail.com. Thanks for reading!